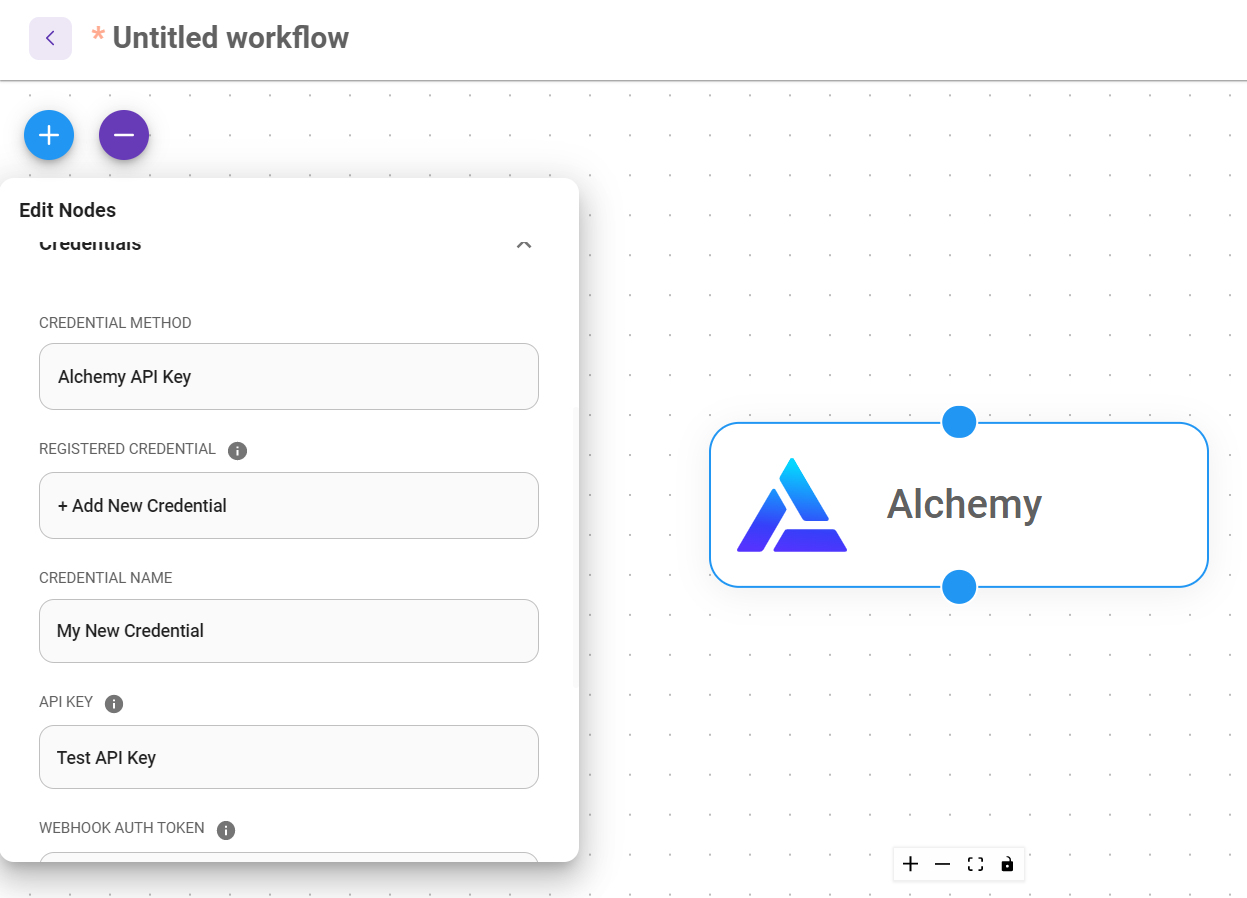
Credentials
Some nodes need to be authenticated to perform an action. For instance, API & Secret keys, Bearer Token, Email password and etc. User can create a new set of credential to store these sensitive information. Credentials will be encrypted and stored in database. Credentials will automatically get decrypted when testing the node or when the node is executed in a deployed workflow.
How credentials are encrypted and decrypted
By using an encryption key. An encryption key is generated using an environment variable PASSPHRASE.
To change the default value:
- Go to
Outerbridge/packages/server - Create one
.envfile or modify the existing one by setting:
PASSPHRASE=<YOUR NEW PASSPHRASE>- Rebuild the app
yarn run build
Encryption key will be stored under Outerbridge/packages/server as encryption.key.
Encryption key is extremely important, make sure it is stored at secured location. For cloud services like AWS, consider using AWS KMS to rotate the key.
Under the hood
Outerbridge uses PBKDF2 to generate an encryption key. AES256 is used to encrypt/decrypt credentials.